Vista – Disable the UAC (User Account Control)
The purpose of this page is to explain how to disable the UAC, Vista’s nagging ‘Continue’ pop-up dialog box.
For security, whenever you need to configure Vista settings, you need elevated privileges – even if you are logged on as the administrator. Before you can complete an administrative task, the User Account Control manager pops-up with a ‘Continue’ message.
Topics for UAC in Windows Vista
- How to Disable UAC (User Account Control)
- New UAC in Windows 7
- Disable UAC in Windows 8
- Registry Hack to control User Account Control
- Example of User Account Control (UAC)
- New Security Philosophy
- Evolution of Vista User Account Control
- CMD Prompt – Run as Administrator
- Disable UAC in Server 2012
♦
How to Disable User Account Control (UAC)
If you feel a little guilty in turning off UAC – join the club. Most people:
a) Get rid of the irritating ‘Continue’ pop-up message box.
b) Feel shamefaced at disabling this Vista security feature.
- Local Policy – Elevate without prompting
- Run all administrators in Admin Approval Mode
- Method for Non-domain Users
- Registry Hack – ConsentPromptBehaviorAdmin
- How to Activate the Hidden Vista Administrator Account
Local Policy – Elevate without prompting
For computers that have joined an Active Directory domain, ‘Elevate without prompting’ is the best Local Policy method for disabling the UAC pop-up. For Vista Home Editions, or any Vista’s not joined to the a domain see below.
Stage 1) Preliminary task:
Our first task is simply to launch the Local Security Policy snap-in. You have the choice of two methods:
Method A) Begin by clicking on Vista’s Start button, then type secpol.msc in the Start Search dialog box. Note: you must include the .msc extension.
Method B) Display Vista’s Administrative Tools. right-click the Taskbar, select Properties, Start Menu, Customize, Advanced; scroll to the bottom and find System Administration Tools, place the radio button next to ‘Display on the All Programs menu’.
Stage 2) Configure the Security Options
- Open the Local Security Policy (See Method A or B above)
- Expand the Local Polices Folder See the screenshot opposite.
- Drill down to Security Options folder.
- Scroll down, and locate the family of settings beginning with ‘User Account Control’.
- Focus on: User Account Control: Behaviour elevation prompt for administrator. Double click and set to: Elevate without prompting. Check the screenshot to the right.

- Restart you Vista computer.
- When the computer restarts, try to configure a tasks that needs UAC. For example, change the computer’s display name. Press the Windows Key + Pause / Break. Select the ‘Change Settings’ shield..
- UAC should now be turned off, thus you should not see the ‘Continue’ box.
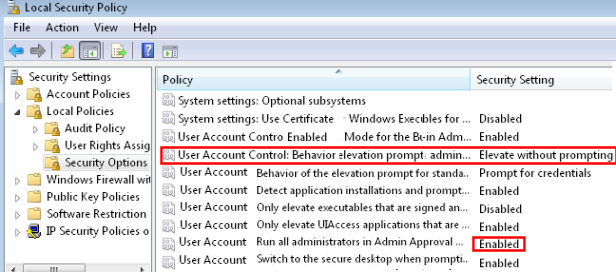
Run all administrators in Admin Approval Mode
There is an alternative, if inferior, method of turning off UAC, that is by disabling the Local Policy, Security Option: ‘Run all administrators in Admin Approval Mode’. Double click and set to ‘Disabled’. Unlike the Elevate without prompting technique, this method turns off UAC and compromises security. My advice is leave this setting as Enabled, and focus on the above setting:
User Account Control: Behaviour elevation prompt for administrator.
Guy Recommends: A Free Trial of the Network Performance Monitor (NPM) v11.5
v11.5
SolarWinds’ Orion performance monitor will help you discover what’s happening on your network. This utility will also guide you through troubleshooting; the dashboard will indicate whether the root cause is a broken link, faulty equipment or resource overload.
What I like best is the way NPM suggests solutions to network problems. Its also has the ability to monitor the health of individual VMware virtual machines. If you are interested in troubleshooting, and creating network maps, then I recommend that you try NPM now.
Download a free trial of Solarwinds’ Network Performance Monitor
Other User Account Control (UAC) Settings
As you can see in the above screenshot, there are more server policies for the UAC. However, they are less important and control specialist situations, for example, installing applications.
User Account Control: Detect application installations and prompt for elevation. For home users, the default is Enabled, meaning home users get a UAC dialog box. However, for domain users this UAC is disabled so that installation can proceed silently.
There are similar UAC Policy settings for Users rather than Administrators.
Only elevate UIAccess applications that are installed in secure locations
The idea behind this policy is that Vista will only give UIAccess privileges and user rights to executables that are launched from %ProgramFiles% or %windir%. The permissions are set on these directories to ensure that the executable is not user-modifiable (which would otherwise allow elevation of privilege).
Registry Change to User Account Control
Group Policy settings ultimately work by changing the registry settings. It follows that you could edit the registry directly rather than configure through the Local Policy GUI. When you are learning and if there is a GUI, that is always the best place to start. However, there may be occasions when you need to go to the registry, for example to create a .Reg file. If you would like to examine the key UAC registry settings, then See more about ConsentPromptBehavior here.
One of the underlying computer dilemmas is productivity versus security. If Microsoft make UAC too difficult, then Administrator’s will investigate registry hacks that make their jobs easier, even if easier means a less secure environment. On my test network I move the imaginary productivity -v- security slider to ease of use, whereas for customers, I move the same slider over to more secure settings.
Disable the UAC – Method for Non-domain Users
In the case of Vista Machines which are not joined to a domain, Microsoft provide a menu in the Control Panel whereby you can turn UAC off. What can I say? You should not use this setting? That would be hypocritical; as someone who loves AutoAdminLogon for non production machines, then unsurprisingly, Guy will uncheck the box ‘Use User Account Control…’ If you would like to turn off UAC, then navigate to: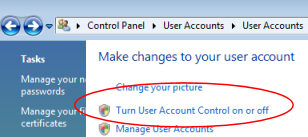
- Control Panel -> User Accounts ->
- Turn User Account Control On or Off.
- Now decide if you want to untick the box which say: ‘Use User Account Control (UAC) to help protect your computer’.
- Now you have disabled the User Account Control.
As I often say, my role is to show you the settings and help you to make informed decisions. In this instance your decision is this: does the security risk outweigh the irritation of having to click ‘Continue’ every time you wish to perform an administrative task?
CMD Prompt – Run as Administrator
My problem occurred when I wanted to run the command: ipconfig /release. What I received was this error message:
‘The requested operation requires elevation’.
Fortunately, the solution was easy; as you can see from the screen shot to the right, just right-click the Command Prompt and select Run as administrator from the shortcut menu. As a result I was allowed to run ipconfig /release. There was no irritating: ‘The requested operation requires elevation’.
An Even Better Solution – Tick Advance Box
When you have found a good move in chess or bridge, always look for a better one. Applying this principle to the CMD prompt:
Right-click the command prompt icon, Properties
Select the Shortcut (tab)
Click on Advanced (button)
Tick: Run as administrator (See screen shot)
Recommended: Solarwinds’ Permissions Analyzer – Free Active Directory Tool
I like thePermissions Analyzer because it enables me to see WHO has permissions to do WHAT at a glance. When you launch this tool it analyzes a users effective NTFS permissions for a specific file or folder, and takes into account network share access, then displays the results in a nifty desktop dashboard!
Think of all the frustration that this free SolarWinds utility saves when you are troubleshooting authorization problems for user’s access to a resource. Give this permissions monitor a try – it’s free!
Download SolarWinds’ Free Permissions Analyser – Active Directory Tool
Overview of UAC
Vista’s User Account Control (UAC) enables you to wear two ‘hats’. Firstly, when you logon as an administrator, you can run applications such as Outlook, but in the context of an ordinary user. Secondly, whenever you need to put on your Administrator’s hat, UAC prompts you the necessary rights, all you have to do is click ‘Continue’ and receive permission to complete that one task.
An Example of User Account Control (UAC) 
Let us consider this situation, you needed to install a driver, Vista presents you with a dialog box. After reading the UAC menu, you click: ‘Continue’ and thus receive elevated rights for the duration of the task. The key concept is you don’t have to logoff and logon as an administrator. Instead Vista just switches tokens, performs the named task, and then returns you to normal user status.
As an example of UAC in action, let us assume that you wish to check the new System Restore settings. You launch the System Icon, (Windows Key and Pause / Break) then you click on ‘System Protection’ and up pops a Windows Security box – even if you are the Administrator. To gain the elevated rights needed to complete your mission, just click the ‘Continue’ button. See screen shot below.
A good habit to cultivate is always to check that the program specified in the central band, is the program you intended; in this case, ‘Change Computer Settings’. Beware that if you are connected to the internet, then sites may have rogue programs that mimic this menu and trick you into installing Spyware.
Microsoft’s New Security Philosophy
UAC is a central plank in Microsoft’s new security fortress. As with so much of Vista, Microsoft has redesigned what an ordinary user, or a base-level user can do. Surprisingly, some security settings have been loosened; if a task does not pose a security threat then Vista lets an ordinary user perform that task. For example, in Vista users can now alter the Keyboard, mouse or adjust the Power Settings. As a consequence, this increases the range of activities for a user, and reduce the number of tasks that require Administrative rights, and consequently the need to display the UAC ‘Continue’ dialog box. Naturally if you feel that certain users are getting too much power, then you can clip their wings with Group Policies, which are now increased from 1,500 in XP to 3,000 in Vista.
Incidentally, Microsoft use this User Accounts Control system to underpin the Parental Controls on the Home editions of Vista. See more on attitudes to the UAC
How User Account Control (UAC) works
If you are familiar with concept of Kerberos in Windows Server 2003, you may already know that once a user logs on successfully, the operating system supplies them with a security token. That token has their privileges and group membership. The whole idea is that the user does not have to keep typing in their password every time they need to open a file or print.
User Account Control extends this idea by supplying what some call a split token and other call two tokens. What ever the semantics, the idea is that to perform jobs such as checking their email or updating their spreadsheets, the Administrator relies on the lesser token, the one with minimal rights. Suppose that same user account now needs to carry out a higher level administrative task, for example, changing a DNS record or amending a DHCP scope option; at this point they need to switch to the other full token, known as Administrator Approval Mode. Thanks to User Account Control, a menu appears with a shield symbol and the clicks ‘Continue’, job done, no need to logoff as a user and the logon as the administrator.
User Account Control – Under the Covers
Imagine a user launching a snap-in from the MMC. The Windows Vista shell calls CreateProcess, which then queries the application to see whether it requires elevated privileges
If the application does not require elevated privilege the process is created through NtCreateProcess – end of story. However, let us assume that the snap-in requires elevated privilege, in this instance CreateProcess, returns an error to ShellExecute.
Next, ShellExecute calls Application Information Service (AIS) and now initiates an elevated launch.
AIS then prompts the user for a password through the Consent User Interface.ShellExecute now tries again, but this time uses the full token to launch the application on the client’s Vista machine.
Evolution of Vista User Account Control
In earlier Beta 1 builds of Windows Vista, UAC was called UAP (User Account Protection). More than just a mere change of acronym, this indicates that UAC is part of a larger security area, which Microsoft are rapidly evolving. Following feedback from beta testers, Microsoft fine tuned the balance between high security and ease-of-use for the UAC.
Microsoft’s press releases tell us that User Account Control is a development of least-privilege user access, or LUA. My view is that User Account Control has grown out of the ‘Run as..’ feature of Windows Server 2003 or the ‘Switch User’ feature of XP. I have to say that at least on training courses, RunAs was one of the least liked features of Windows Server 2003.
Even when we ignored ‘Run as…’ on those training courses, we had this feeling of being naughty boys and not taking security seriously. User Account Control makes it easier to develop good habits and work securely. UAC is like opening a locked draw using a plastic card kept in your top pocket, compared with ‘Run as…’, which is like walking over to the filing cabinet and finding the correct key for your draw. In summary, User Account Control automatically gives you the best of both worlds, rely on a basic token for routine tasks and reserve the Administrative token for special security responsibilities.
Surprise, I discovered that certain tasks still need the ‘Run as…’ technique, for instance releasing and renewing an IP address. This is how it works.
Summary of User Account Control (UAC)
User Account Control (UAC) is a central plank in Microsoft’s security platform for Vista. This page gives you strategies for controlling this service. One theme that runs through UAC is that Microsoft are still fine-tuning the places where you can configure the settings, there have been significant changes from Beta 1 –> Beta 2 –> RC1 –> Vista Final Release.
If you like this page then please share it with your friends
Windows Vista Security:
Other Sections |