Windows Vista – Security
I will never be able to shake off the ‘Country Boy’ attitude to security; the reason is because where I came from, we left the back door open and the keys in the car’s ignition. Thus if Vista’s new security features such as service hardening appeal to me, then they must have merit.
Windows Vista Security Topics
- Restrict privileges with UAC (User Account Control)
- ConsentPromptBehavior
- Windows 8 Disable UAC
- How to Activate the Hidden Vista Administrator
- Windows Service Hardening
- Internet Explorer 7 (IE7)
- Parental Controls
♦
Other Vista Sections
- Vista Configuration
- Vista Preparation
- Vista Registry
- Vista Troubleshooting
- If you haven’t found what you are looking for, try the index page
Restrict privileges with User Account Control
One security strategy that Windows Vista enforces is that every program, even those of the administrator, run with minimal privileges. What happens in the case of the administrator is when a program needs extra privileges, then the User Account Control manager warns and waits for confirmation before completing the action. The advantage of Vista’s new method is that if a virus seeks to gain control it would have to ask the User Account Control manager, at which point you would be alerted and decline the action.
I wish Microsoft’s User Account Control system well, I only hope that my two fears never materialize. Firstly, I fear that it’s only human nature to be lulled by the User Account Control manager, so that even if a virus triggered it, the average person would still OK the action. My second fear is that a virus writer would find a back door to suppress the dialog box, or alternatively they would develop a method of programmatically clicking on the OK button. See more on User Account Control
Windows Service Hardening
What Microsoft mean by Windows Service Hardening is reducing the scope Windows Services and this improving security. Windows Services no longer have limitless rights and scope, instead it has only the rights needed to do its job. In the past, hackers have attacked via Windows Services. In Vista these hackers are in for a surprise, even if they were able to successfully hi-jack a service such as Telnet or SMTP, the new ‘hardening’ means they have no scope for their nefarious deeds.
Allied to windows service hardening is registry restriction. The idea is that normally, Vista only exposes a subset of the registry to a program or service. However the administrator can still see the whole registry with regedit.
Recommended: Solarwinds’ Permissions Analyzer – Free Active Directory Tool
I like thePermissions Analyzer because it enables me to see WHO has permissions to do WHAT at a glance. When you launch this tool it analyzes a users effective NTFS permissions for a specific file or folder, and takes into account network share access, then displays the results in a nifty desktop dashboard!
Think of all the frustration that this free SolarWinds utility saves when you are troubleshooting authorization problems for user’s access to a resource. Give this permissions monitor a try – it’s free!
Download SolarWinds’ Free Permissions Analyser – Active Directory Tool
Internet Explorer 7 (IE7)
Traditionally, Internet Explorer (6.0) has been the greatest source of Malware, so reducing the privileges in IE7 is one of the most effect security strategies. (Following the lead of reduced privileges for programs and service hardening.)
Using different techniques, IE7 identifies Phishing sites. However, the cynic in me says that the bad people won’t stand still and they will come up with new scams. Remember that IE7 won’t be the magic bullet. As Sergeant Phil Esterhaus of Hill Street Blues used to say: ‘Let’s Be Careful Out There’.
A balanced opinion would say that IE7 is a lot better than anything we have had before, and hackers and scam merchants will pick on the weakest link and that is IE6. See more on Internet Explorer 7.
Parental Controls
To enable Parental Control, I would open IE7, then navigate: Tools, Internet Options and Content Tab. Now you should see ‘Choose a user and setup Parental Controls’. Alternatively, you could head for the Control Panel, User Settings and click on Parental Controls.
Parental Control strategies, either select predefined categories such as Web chat or Gambling, or add specific sites that you don’t want children to surf. If you already use Junk E-mail settings in Outlook you will soon understand how to block specific sites.
The child soon realizes that the site has been blocked the browser display a HTTP 450 error (File unavailable), if the parent was sitting near them, and the site was suitable, they could ask the parent to display the page simply by typing their password. However, I as a parent, I would not do this as savvy children will watch the keyboard and memorise the password as they see you type it!
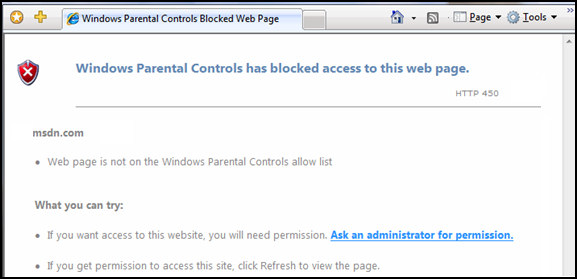
Parental Controls can also block downloads, look for a check box right at the bottom of: ‘Choose a user and setup Parental Controls’.
Guy Recommends: A Free Trial of the Network Performance Monitor (NPM) v11.5
v11.5
SolarWinds’ Orion performance monitor will help you discover what’s happening on your network. This utility will also guide you through troubleshooting; the dashboard will indicate whether the root cause is a broken link, faulty equipment or resource overload.
What I like best is the way NPM suggests solutions to network problems. Its also has the ability to monitor the health of individual VMware virtual machines. If you are interested in troubleshooting, and creating network maps, then I recommend that you try NPM now.
Download a free trial of Solarwinds’ Network Performance Monitor
Summary of Vista Security
The wide ranging and detailed measures that Microsoft has take to make the operating system secure underpin every aspect of Vista. From controlling actions with UAC, through service hardening to registry restriction, Windows Vista offers top to bottom security. Not only has each component been redesigned from scratch, but redesigned with security in mind.
If you like this page then please share it with your friends
Configuring Windows Vista Topics:
| Vista Tools and Extras
|
Download Your Tweak the Registry Ebook for only $6.45 This ebook will explain the workings of the registry. I thoroughly enjoy tweaking the registry, and I want to distill the best of my experiences and pass them on to you. Each registry tweak has two aims; to solve a specific problem, and to provide general learning points, which help you to master regedit. Over 60 pages ebook and PDF format
| |



