
Our personal and professional lives are becoming more and more digital. While this trend has a number of upsides ranging from optimized workflows, to better connectivity with loved ones, to Netflix binges, it also means the importance of network security is at an all-time high.
One of the cornerstones of a secure network infrastructure is the ability to identify and mitigate threats before they compromise data or bring down a network. A strong Intrusion Protection System (IPS) or Intrusion Detection System (IDS) can play a major role in doing just that.
In this article, we’ll dive into the topic of IPS and IDS, review some of the basic concepts including SIEM, and then provide an overview of some of the popular SIEM, IPS, and IDS software available for Windows, Linux, and Mac OS. If you’re already comfortable with the basics surrounding intrusion prevention and detection, feel free to
Here is our list of the top network intrusion detection tools:
- SolarWinds Security Event Manager (FREE TRIAL) This SIEM tool gathers activity reports from around a network and scours them for signs of intruder activity. Runs on Windows Server.
- CrowdStrike Falcon Firewall Management A cloud-based package that interacts with on-site firewalls to identify and block intrusion.
- SNORT A free IDS that is maintained by Cisco Systems and operates as a packet sniffer. Runs on Linux, Unix, and Windows.
- Security Onion This is a compendium of free intrusion detection systems that bundle into a single package. Runs on Linux.
- Zeek This free network monitoring tool used to be called Bro and it has an active user community that provides advice on how to tune the tool. Runs on Linux, macOS, and Unix.
- OSSEC Open Source HIDS Security is believed by many to be the original SIEM tool and it is still free to use. Runs on Windows, Linux, Unix, and macOS.
IPS Defined
An IPS is an IT security system that monitors a network for malicious activity and proactively attempts to mitigate or prevent the threat.
In some cases, IPS solutions are dedicated hardware appliances that run powerful IPS software and are deployed as discrete nodes within a network. Cisco’s Firepower NGIPS (Next Generation Intrusion Prevention System) product line includes a number of hardware devices that fit this description.
Differences between IPS & IDS
You may hear the terms IPS and IDS used interchangeably. Given that many security solutions support both and IPS is sometimes referred to as “proactive IDS” or similar, the confusion is understandable. The main difference between IPS & IDS is exactly what the names imply: an IPS attempts to take action against intrusions while an IDS only detects them.
There are pros and cons to both approaches to intrusion detection. In short, the tradeoff is summarized as one between automating responses (which an IPS can do) and minimizing the effects of false positives (of which an IDS would have less).
HIPS & NIPS
At a high level, there are two ways to deploy intrusion prevention (and detection) systems: at the host-level or at the network-level. The host-based systems are referred to as HIPS (Host Intrusion Prevention System) and network-based systems are referred to as NIPS (Network Intrusion Prevention System). For their IDS counterparts, HIDS and NIDS are the acronyms used.
HIPS are installed on a given host (e.g. a personal computer) and only protect that host. NIPS are installed on the network and protect multiple systems on the network.
HIPS vs Antivirus
There is a lot of confusion and ambiguity as to what exactly differentiates an HIPS and antivirus software. One somewhat popular way to separate the two categories: a HIPS looks at behavior, files, and changes to a system while an antivirus software just looks for malicious or unwanted files. However, this falls apart a bit as you begin to take a look at what most modern antivirus software actually do. Many antivirus perform features fall into the aforementioned “HIPS” category. Within the context of this article, we’ll look at some software that calls out host intrusion prevention specifically to help give you an idea of what’s available on the market and how it stacks up to antivirus software.
A NIPS is NOT a firewall
It is important to understand that an IPS is NOT a firewall. Firewalls provide a different type of rule-based security that is important and should not be overlooked, but there are many threats that do not violate firewall rules. That is where IPS and IDS comes in. For example, a firewall can stop traffic HTTP traffic to port 80 altogether, but it isn’t designed to analyze the content of network packets and take action if something malicious is detected. That’s where NIPS comes in.
However, there are products that combine the functionality of a firewall and an NIPS into one device. Cisco’s Next Generation Firewalls (NGFWs) are a popular example.
How are threats detected?
There are two popular methods used by IPS and IDS to detect threats, signature-based detection and anomaly-based detection. Signature-based detection compares traffic to a database of known threat definitions while anomaly-based detection uses heuristics. While anomaly-based methods offer some advantages in the form of detecting zero-day or otherwise undefined threats, they are also generally more difficult to develop and maintain.
What is SIEM?
Security Information and Event Management software products, or SIEMs, are a way to centralize and analyze network security data and help scale security solutions. Data from nodes running IDS or IPS software can play a big role in getting the most out of a SIEM solution. SIEMs help make IPS and IDS more scalable and can better enable organizations to achieve compliance, improve reporting, and identify correlations that can indicate a broader threat. In short, SIEMs enable organizations to scale their IDS and IPS data into a more complete security solution.
The best Network Intrusion Detection Tools
Now that we have established an understanding of IPS, IDS, & SIEM, here is our list of the best SIEM, IPS, & IDS tools:
1. SolarWinds Log & Event Manager (FREE TRIAL)
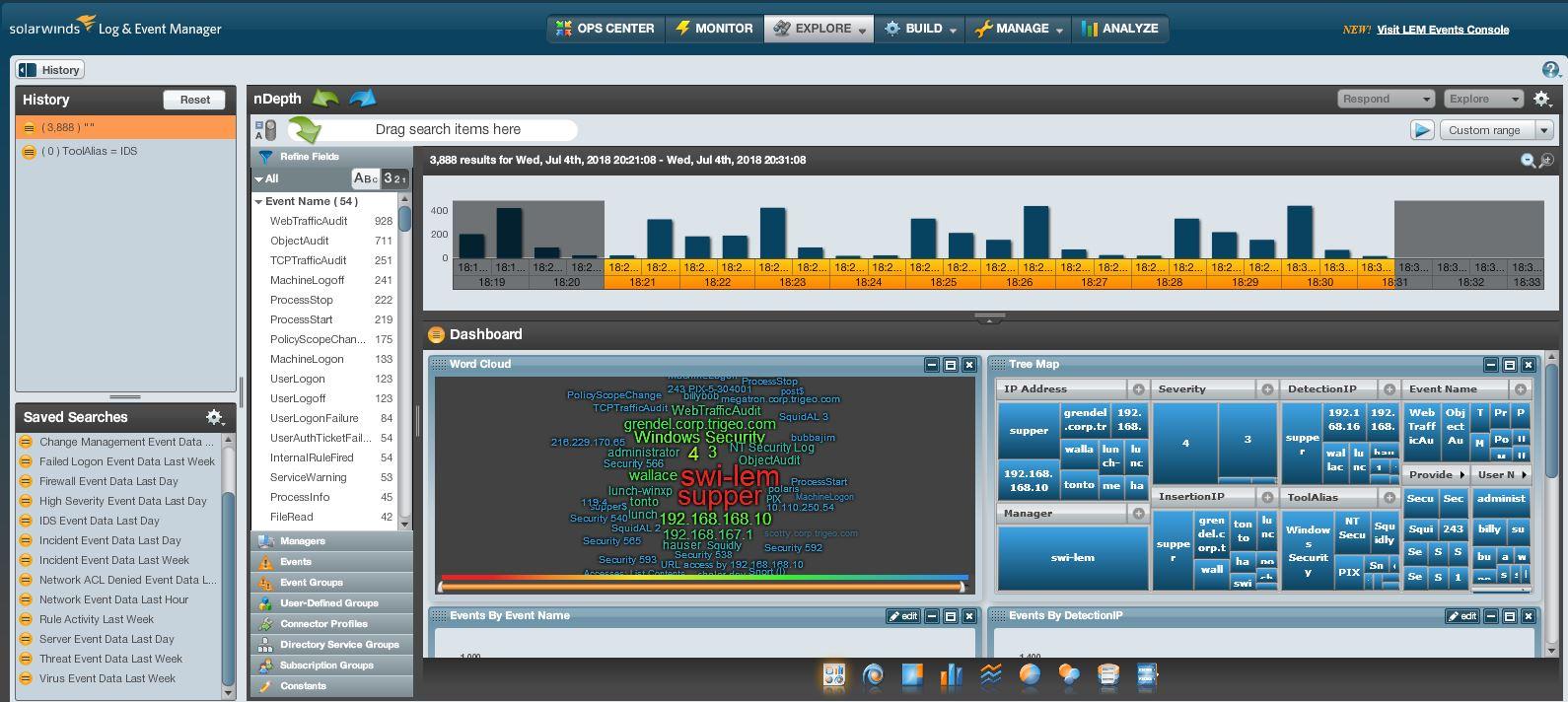
SolarWinds Security Event Manager (SEM) is an enterprise log management solution. SEM is deployed as a virtual appliance on VMware vSphere or Microsoft HyperV hypervisors. SEM offers advanced reporting and monitoring to help scale and centralize your network security administration. Given its advanced feature set, SEM is often used as a SIEM. SEM supports dozens of IPS and IDS connectors from a variety of vendors including Cisco, Juniper, and Trend Micro. You can view the complete list here.
The nDepth search engine included with SEM adds a significant amount of extensibility and functionality. As an example, check out this article describing how you can create an nDepth query to display all activities by a given user.
For a deeper dive into SolarWinds Security Event Manager check out our review. To test drive SEM yourself from a browser, click here.
2. CrowdStrike Falcon Firewall Management

CrowdStrike Falcon Firewall Management takes the stance that network activity only becomes harmful once it reaches an endpoint. As the firewall of an endpoint is its interface to the network, tracking firewall activity provides reports on network activity. This is an efficient approach but it leaves network devices unprotected, so you should also perhaps invest in a network configuration manager if you decide to use CrowdStrike Falcon Firewall Management as your network protection solution.
This system is based in the cloud. It operates in conjunction with CrowdStrike Falcon Prevent, which is an on-device anti-virus system. The Prevent installation acts as an agent for the firewall manager vehicle simultaneously providing endpoint protection behind the device’s firewall.
The CrowdStrike Falcon Firewall Management tool lets you set security policies that influence the settings of firewalls and dictate how they scan and block traffic. You can define policies for individual firewalls, groups of firewalls, or all of your firewalls. The system can manage firewalls running on Windows and macOS. Start a 15-day free trial.
3. SNORT

SNORT is one of the biggest names in IPS and IDS. SNORT’s Network Intrusion Detection System Mode enables you to define if SNORT blocks or just alerts when a thread occurs. This choice is what determines if you’re using SNORT as an IPS (blocking) or IDS (alerting). SNORT can also operate in Sniffer Mode as a packet sniffer or Packet Logger Mode as a logging solution.
For the most part, SNORT uses signature-based detection. There are a wide variety of base policies within SNORT. Additionally, for advanced users SNORT allows you to write your own policies.
SNORT is open source and has a large community of users. It is used as a part of enterprise security solutions (e.g. Cisco’s 4000 Series Integrated Services Routers), so it’s also a good reference for those of you looking to get familiar with enterprise tools without access to enterprise hardware.
SNORT is supported on Windows, Fedora, Centos, and FreeBSD.
4. Security Onion
Security Onion is a Linux distribution designed to serve as a security solution that includes network-based IDS and IPS. Security Onion leverages a number of popular security solutions like OSSEC, SNORT, Suricata, Elasticsearch, Logstash, Kibana, Bro, Sguil, Squert, NetworkMiner, and a number of other tools for network security. A configuration wizard helps make provisioning easier for first time users. You can download the Security Onion ISO for free here.
5. Zeek

Zeek was originally called Bro and it is a data scanner that works as a network-based intrusion detection system. The tool relies on a network packet sniffer to provide a feed of traffic data, which it then searches through for signs of intrusion. It is possible to set up rules that will trigger on the detection of a particular type of activity, which makes this an IPS.
You can get enhancements from the active user community. That community is also your main source for advice and support because this is a free, open source system and isn’t supported by a professional team.
The system doesn’t have its own data collector, log file manager, or front end, so it will appeal to administrators who love a technical challenge. Small businesses that don’t operate within the field of technology won’t have the appropriate skills on site to set Zeek up.
Zeek runs on Linux, Unix, and macOS, and you can download it here. The tool is one of the components of Security Onion, so that gives you another option for accessing this package.
6. OSSEC

OSSEC is a free and open source (released under GNU General Public License version 2) HIDS that supports a wide variety of operating systems including Windows, macOS, FreeBSD, OpenBSD, Linux, AIX, and VMware ESX.
OSSEC supports monitoring of files and logs, rootcheck, and process monitoring. Alerts from OSSEC can be sent via email or syslog for integration into a SIEM system. OSSEC has a large community of users and developers supporting it which can be helpful when you’re just getting started with a new tool.
For more on OSSEC, check out their detailed documentation pages.
Summary
Securing your IT infrastructure using SIEM, NIPS/NIDS, and HIPS/HIDS can help keep your business running and mitigate risk. In this article we discussed some of the nuts and bolts of intrusion detection and prevention and provided an overview of some of the top SIEM, IPS, and IDS software available today.
What did you think of our choices? Is there anything we left out? Do you have a question about one of the tools mentioned here? Let us know in the comment section below.


