SolarWinds Remote Execution Enabler for PowerShell
It's been fascinating to observe how the computer community has embraced PowerShell. Some techies write their own scripts, others use modules created by developers, while lesser mortals may not realize that PowerShell is at the heart of their Windows utility.
For all these PowerShell aficionados there is one problem, which gets often gets swept under the carpet – namely the difficulty of running scripts remotely. Fortunately, thanks to SolarWinds, we now have a solution to this frustrating problem: – Remote Execution Enabler for PowerShell.
The Key to Remoting: WinRM (Windows Remote Management)
WinRM is Microsoft's implementation of WS-Management Protocol. Its purpose is to provide a SOAP-based (Simple Object Access Protocol) that enables hardware from different vendors, to work together. It also allows us to run scripts remotely on dozens of machines simultaneously, rather than looping through one script while substituting the names of multiple servers.
In other words, WinRM allows you to communicate, diagnose, and even control remote devices. Depending on your computer background you may think that WinRM is a great opportunity, or, it's a security nightmare.
In reality WinRM is like using a RPC (remote procedure calls), however, the security is so difficult that ordinary users struggle to it working with their PowerShell scripts. Hence the need for a utility such as SolarWinds Remote Execution Enabler for PowerShell.
Components of WinRM Windows Remote Management
I list the various WinRM components merely to explain the complexity of managing devices, remotely, and thus explaining why it's a task crying out for a third party tool such as Remote Execution Enabler for PowerShell.
1) WS-Management Protocol – A public standard for remotely exchanging management data.
2) WS-Management Objects
- Enumerator
- ConnectionOptions
- Session
- ResourceLocator
- WSMan – Provides methods and properties used to create a new session or manage an established session
3) WMI Service
4) WSMan Service
5) Finally, there is the tricky server-side component WinRS (Remote Shell).
PowerShell's Own Remote Offerings
You can run many PowerShell scripts against remote machines by simply appending the -ComputerName parameter, for example:
Get-Service -ComputerName BigServer.
However, using cmdlets that create a persistent pipe to the second machine is much more difficult, but rewarding. Conceptually there are four tasks to create true remoting with PowerShell
- Check WinRM is installed.
- Enable PowerShell Remoting.
- Set TrustedHosts *
- Create a Remote Session with PSSession.
I have spent hours using PowerShell's own commands to configure WinRM and WSMan, on occasions I have had success in connecting to a remote machine. Yet when I tried again the next day, it seemed like the unrepeatable experiment, and I was back at square one.
For a long time I thought these difficulties were down to my inadequacy, but researching forums such as Stack Overflow revealed that I am not alone in struggling to run PowerShell scripts remotely.
Installing the Remote Execution Enabler for PowerShell
They often call me 'Gung-ho' Guy because I like to install utilities by just clicking through their menus. My credo is that all software should just work without me having to read the manual.
So, I downloaded SolarWinds Remote Execution Enabler for PowerShell, noted that it would install as a Windows service, then I launched it.
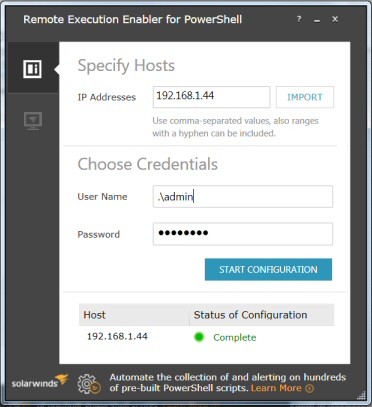
At my Windows 8 machine, I typed in my own IP address, my own admin account with password, and waited…. Failed. Invalid Credentials.
O.K, time for me to read the help file. Ah-ha, if you're not in a domain then you must type dot backslash before the name. Hence .\Admin. Just to reinforce this point, use plain .\Admin, and not MachineName\Admin.
Success! Green light, Host Status Complete.
The target system is now able to accept remote PowerShell commands.
Now we are ready for the next step, namely to use this delightful SolarWinds tool to configure multiple machines so that they can receive remote PowerShell commands; for example an IP range such as: 10.5.1.21-99
Testing the Configuration of TrustedHosts
Under the covers this Remote Excecution Enabler for PowerShell changes the settings for TrustedHosts from its default of null meaning nobody is trusted to –> * meaning all connections are trusted.
I anticipate that you have done a risk assessment, and want to prepare a batch of computers to accept connections, which will run your PowerShell commands remotely.
To double check the configuration change has worked, launch PowerShell and run these commands.
cd wsman::localhost\client
dir
Note the result: TrustedHosts *
Experiment for Sceptics
Run this command below from within PowerShell; observe how the TrustedHosts value of "" reverts to its default value of null.
winrm s winrm/config/client '@{TrustedHosts=""}'
# Check with
cd wsman::localhost\client
dir
Now launch Remote Execution Enabler for PowerShell, and configure it again. If you check the wsman dir one more time, you will find that TrustedHosts has reverted to: "*". [Remember the .\Username]
Troubleshooting Remote Execution Enabler for PowerShell
You may also encounter these Error Codes:
- Admin share is not available.
- Cannot check or enable firewall rule
- Empty arguments list
- Invalid arguments count
- Invalid credentials
- PowerShell 2.0 is not installed
- Unable to create a WSMan listener
- Unable to create self-signed certificate
- Unable to detect group membership
- Unable to detect PowerShell version
- Unable to reuse an existing WSMan listener
- Unable to set up PowerShell language mode setting
- Unable to set up Windows authentication
- Unable to start WinRM service
- Unknown host
Incidentally, I found that you can substitute the hostname for the IP address.
Testing PowerShell Commands
# PowerShell PSSession
New-PSSession -ComputerName testMachine2
Get-PSSession
# Remove # On next line if you want to delete a Session
# Get-PSSession | Remove-PSSession
Another Tactic – SolarWinds Server & Application Monitor (SAM)
I love the way SolarWinds produce a nifty free utility such as Remote Execution Enabler for PowerShell, then support it with a "big brother" application with all the bells and whistles. In this instance, their Server & Application Monitor (SAM) provides the extra features large organizations need to automate managing hundreds of pre-built PowerShell scripts.
Highlights of SolarWinds SAM
- Dashboards to consolidate important metrics in one view.
- Monitor all your commercial and in-house applications.
- Troubleshoot and resolve problems using the Web console.
- Multi-vendor support and lifecycle management.
- Get a Free trial of SAM (Fully functional for 30 days)
Summary: Review of Remote Execution Enabler for PowerShell
You can install, and test, SolarWinds Remote Execution Enabler for PowerShell on your workstation. Then it's away-to-go, and configure remoting on a range of servers or workstations.
Additional Free and Trial SolarWinds Network Software
Here are nifty gadgets which I have enjoyed testing on my network. Some are completely free, while other downloads are trial versions of the full product. I think SolarWinds have a great strategy, namely, supplying a free utility, yet providing a big-brother suite of programs for larger organizations.
• Permissions Analyzer • Review Alert Central • Free NetFlow Analyze • SolarWinds Firewall Browser
• Netflow Monitoring Explained • SolarWinds Web Help Desk • Wireshark Response Time Viewer
• Mobile IT Admin App • Call Detail Record Tracker • VoIP Network Quality Manager • Home